One of the common ways to do two-factor Authentication is to use an authenticator app like Authy, Microsoft Authenticator, 1Password or LastPass Authenticator.
Authy manages one-time passwords
The common denominator of Authy and other apps mentioned above is that they generate time-based one-time passwords (TOTP). They are usually set up like in the screenshot below. You have probably seen it many times:
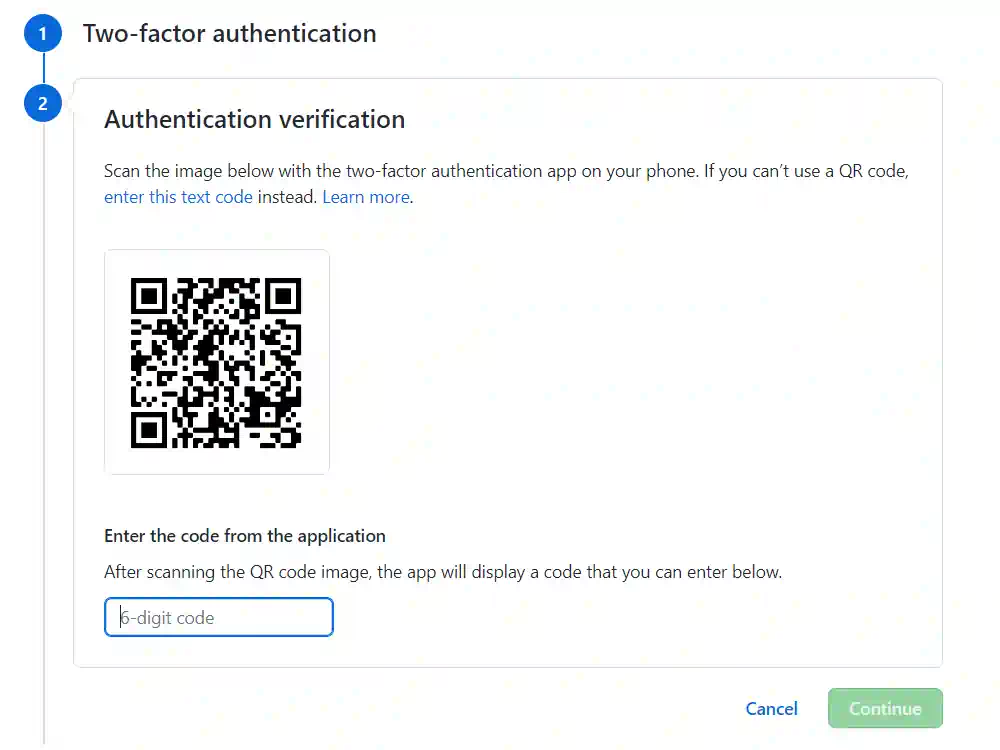
This is a good and secure solution. It appears that it’s also the most popular 2FA method in the sites I visit. Personally, I have such 2FA method configured for 27 services I use! However, I don’t know how about you, but it also generates an annoyance and friction when I need to reach for the phone, find the app, and re-type the 6-digit code to the website 😉
YubiKey device is a bit different
YubiKey device is a bit different. You have probably bought it, or intend to buy, for a very convenient and secure single-touch login. Nowhere in the process you need to type 6-digit codes.
This is because underneath it’s an entirely different protocol called WebAuthn, and not TOTP described previously. A website might support WebAuthn, TOTP, or none, or both.
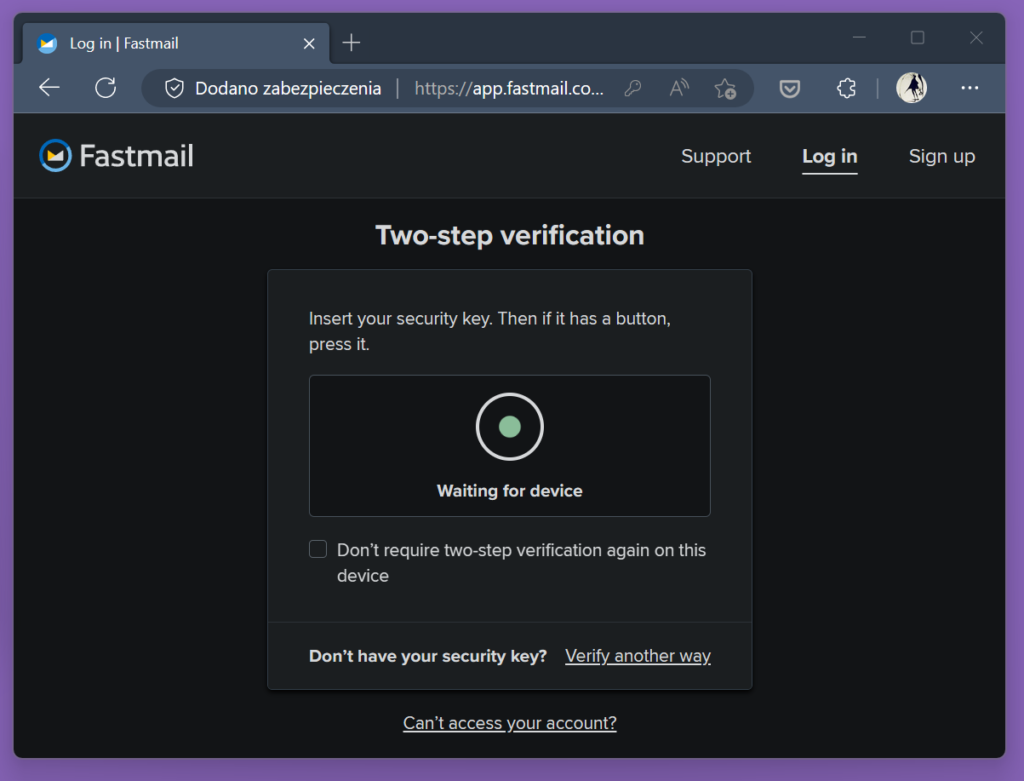
Unfortunately, this means that we cannot simply use YubiKey’s single push of a button wherever we used 6-digit codes. The site must implement the WebAuthn protocol to allow us to use that more convenient method of authentication. Many major sites like Google, Microsoft, GitHub, or Facebook do. But presently, it’s still less common than TOTP and you are unlikely to eliminate the use of time-based codes from your life completely.
See the following Stack Overflow post by Nate Eldredge if you want to understand why YubiKey cannot do some magic and just handle TOTP when you touch the device. The YubiKey device does not have a real-time clock on board, so it cannot generate time-based codes. Moreover, without any software assistance, it wouldn’t know which site is asking for the code and what token to generate.
Yubico Authentication App is yet another thing
It might be a bit confusing now to add that there is an application called Yubico Authentication App, released by the same company that creates YubiKeys.
It makes use of another feature of the YubiKey hardware. Credentials required to generate 2FA codes can be stored on YubiKey device instead of on mobile phone, and this way they are less likely to be compromised. You might take a look at it if you are interested in increased security. But don’t expect any increased convenience – you’ll still have to type the codes 😉

Even though YubiKey 5 isn’t a magic tool that will instantly eliminate time-based one-time passwords from our life, I think it is a wonderful device. Hopefully, the support for the WebAuthn protocol will steadily grow and the future of 2FA will be marked by both security and convenience it provides. If you care about security on the internet and value your convenience, it’s certainly worth to have one (or more) 🙂
